Verifying Your Downloads
You want the program. You researched its reputation. But you're not sure you trust the delivery mechanism.
Community members often download useful programs (like Putty, VBox, Cygwin, Truecrypt, Tor, etc.) from the Internet. Two lingering questions nag the downloader:
- Did my download get corrupted?
- Did the version I downloaded get tampered with by a bad guy?
SHA256 sums and MD5 sums
One way to answer the first question (and, to a limited extent, the second question) is frequently available on the website. In addition to a download link, the site may provide an MD5 or SHA256 sum (hash) string. For example, on July 14, 2012, IrfanView provides, on the downloads page, the following SHA256 sum:
iview433_setup.exe – 7c8af2a762278504ac671d73ce65dad42c6cab435dbda5658a94137acf636b70
I can download it from one of the mirrors, but how do I check it?
When you check MD5 and/or SHA256 sums, you are better assured that – provided the website isn't compromised by a bad guy – your download is consistent with the file intended to be available to you by the presumed good guys that created it.
Linux
From your terminal, just run “md5sum thePath/YourFile” or “sha256sum thePath/YourFile.” and see that the value matches the one on the website.
Windows
If you are running Windows, you can download a utility from Microsoft called Sigcheck. (Google: Microsoft sigcheck). It's a zip file. Humm, Microsoft itself hasn't provided a hash string. (Read ahead to find out how to check it or make a leap of faith and trust the Microsoft sigcheck download for now.) Unzip the file to a known location. You will see a file named “sigcheck.exe.” Copy your downloaded “iview433_setup.exe” file to that folder too. Open a command prompt and change to that directory. Type: “sigcheck -h iview433_setup.exe.” If all goes well, you will see:

Notice that the SHA256 hash string matches the one given on the website.
Digital Signatures
Now, about that sigcheck.exe file that you downloaded. Locate the file from your file manager, right click it, and pick Properties. You should see the following on the Digital Signatures tab:

You see “Microsoft Corporation” under “Name of Signer.” A valid [and trusted] digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit. (Wikipedia). Digital signatures make a stronger statement than consistent hash strings; they are strings created by the author as a result of cryptographically signing the file with a private key. A forger cannot fake the digital signature easily. But, where's the trust coming from?
The sigcheck.exe file actually has a little more than a digital signature. The signature is certified to be a valid signature for Microsoft Corporation by a third party certificate authority (CA). Certificate authorities do not certify that their clients are trustworthy. Rather, they certify that their clients' public keys are known to be the clients'. There are programs that you may want to download from sources that you trust... sources that don't have paid-for certificates. However, some of them do have digital signatures. (Right-clicking them in Windows will not show a Digital Signatures tab under properties because it finds no local certificate.) In these cases, you will have to act like your own CA and supply your personal trust.
Prefer sites that provide digital signatures (A signature (*.sig) file for the download and a public key (*.asc) file for the author). But be careful, you are determining trust.
Windows
One way to do verify digital signatures requires that you (again) download a program. Go to http://www.gpg4win.org/download.html and get GPG4Win. While you are at it copy the SHA256 sum. Check the SHA256 sum with Sigcheck as outlined above. If it checks, you know the download went well. Right click the GPG4Win.exe and select properties. You see a digital signatures tab that shows Intevation GmbH as a confirmed signer (it has a valid digital signature that is certified by a CA). Install the program (skip configuration if you want), and start it up. The first time you run it you can generate a private key, but don't feel compelled.
Let's use GPG4Win to check a download that doesn't verify in Windows. Go to Putty - downloads at http://www.chiark.greenend.org.uk. Also open the “RSA Sig” link, copy the whole page, paste it into Notepad, and save it as Putty.sig. Now, navigate to the “Keys” page on the Putty site. There are six keys. Right-click the “RSA Release key” link and save it as Putty.asc. Open the GPG4Win program and import the Putty.asc key into the GPG4Win Key Manager.

Now, open a command prompt and type:
gpg –verify
yourPath/Putty.sig yourPath/PuttyInstaller.exe.
You
should see something like this:
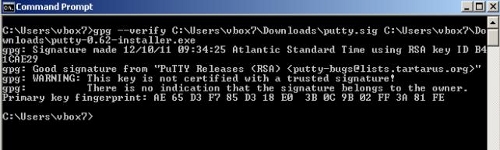
It shows a good signature. It also shows a warning that the key isn't certified as trusted. That means it hasn't been trusted by a CA known to your machine nor has it been formally, on your machine, trusted by you. You can make this warning go away by trusting the Putty.asc public key from the Key Manager. Doing so will not improve the intrinsic trustworthiness of the signature. By downloading it and considering it worthy for verifying a file's signature you have already, perhaps haplessly, given it your trust. Be mindful of how signature files and public keys are delivered (https and check the address).
Linux
With Linux, I prefer to manage keys with the handy Seahorse GUI. Most often, it is already installed on your distribution. If not, sudo apt-get install seahorse. Let's verify a Truecrypt download. Go to the Truecrypt downloads page. Under Linux, pick the standard 32 bit package. Also, click/save the PGP Signature. At the bottom of the page is a link: “Source code, language packs, past versions, public key.” Go there, find “TrueCrypt-Foundation-Public-Key.asc,” and download the link. Open seahorse (type seahorse into terminal) and File → import the Truecrypt.asc file. Now you can verify the download file from the terminal with:
~$ gpg --verify thePath/TruecryptSigFile.sig thePath/TruecryptPackage.tar.gx.

As with the Windows example above, the key is not certified. You are the CA. Use Seahorse to make it a formality if you want.
Using digital signatures is considerably safer than innocently trusting Internet downloads. Having a digital signature is not sufficient for knowing a file is benevolent? Bad guys can have public keys too and there are counterfeit keys that sign counterfeit software.
